!, 2015-10-01 08:26 »

- game_over_by_ventious-d73m9mg.gif (418.05 KiB) Viewed 9001 times
Speaking of the forced updates in Windows 10, which by the way, you won't have to put up with it if you follow my instructions here:
How to disable Windows 10 spyware telemetry logging, including killing off forced Windows updates.
Nerves rattled by highly suspicious Windows Update delivered worldwide.
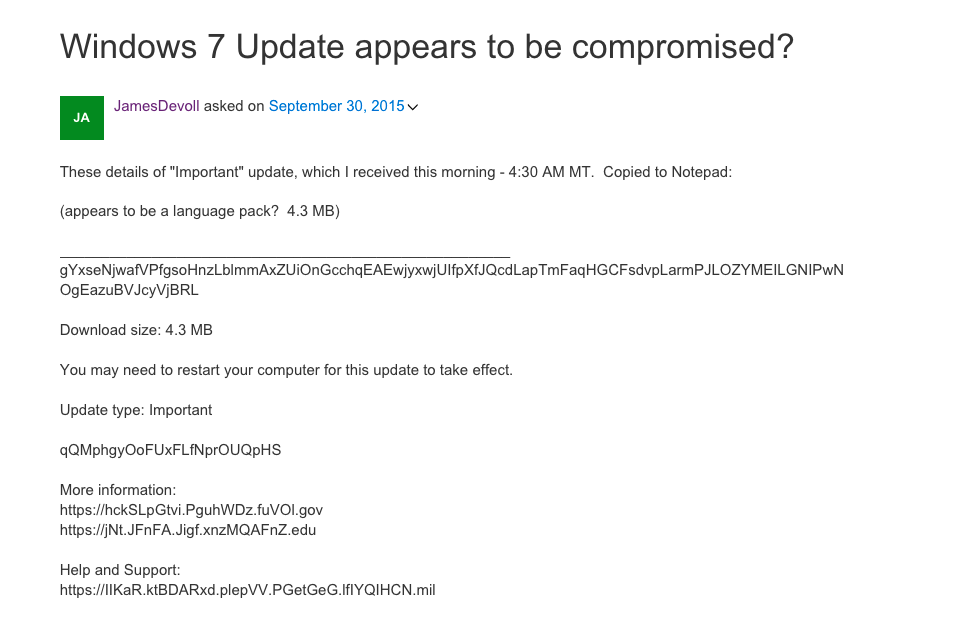
Check out those lovely .MIL and .GOV URLs in this thing! Microsoft said it was an accidental "test". Hahahahhaha riiiight... two ways this could have been:
This wasn't a test, either on purpose or not.
This was a test.
BOTH scenarios are JUST AS BAD!
Bottom line is that Microsoft CANNOT BE TRUSTED TO FORCE AUTOMATIC UPDATES INTO YOUR MACHINES WITHOUT THEM EVEN SAYING WHAT THE MOTHERFUCKING UPDATE IS OR YOU BEING ABLE TO STOP/CHOOSE WHICH UPDATES TO PUT ON YOUR OWN FUCKING MACHINE!
Fuck them!
- suspicious-windows-update.png (87.76 KiB) Viewed 9001 times
Strange payload raised concerns that Windows Update has been hacked.
...
This
Web search, which queries the random-appearing string included in the payload, suggests that it's being delivered to people in multiple regions. The same unexplained and almost certainly unauthorized patch is being reported in a variety of online posts, including this one hosted by Microsoft.
The updates appear to be coming directly from servers that are cryptographically certified to be part of Microsoft's Windows Update system."Clearly there's something that's delivered into the [Windows Update] queue that's trusted," Kenneth White, a Washington DC-based security researcher, told Ars after contacting some of the Windows users who received the suspicious update.
"For someone to compromise the Windows Update server, that's a pretty serious vector. I don't raise the alarm very often but this has just enough characteristics of something pretty serious that I think it's worth looking at."White is still trying to obtain a copy of the binary file that gets delivered to people receiving the update. He plans to run it in a restricted environment to see exactly how it gets delivered and what it does once it's installed. One person reported that the update won't download. White said for those who can get the download to work, the payload should be located at c:windowsmsdownloadupdatesoftwaredefu2015�9 estexe_xxxxxxx.exe (where xxxxxxx is the random-appearing characters found in the update bulletin. A Microsoft spokesman said company officials are investigating the reports.
One user has reported installing the update and finding that it rendered the computer largely inoperable.
"My laptop was screwed after the update," the user, ByGodZombie, reported in a comment to this post. "Windows explorer crashes VERY frequently now and most of my programs stopped working even in admin mode. System restore didn't work and I don't have the information I need for a reinstall. Basically whatever it was killed my system and compromised my gear so I wouldn't want to look up anything sensitive to personal data on your machine."It's hard to patch a machine when the update mechanism is compromised.
Assuming the worst, that Windows Update has been compromised, it wouldn't be the first time. The Flame malware reportedly developed by the US and Israel to spy on Iran hijacked Windows update so it could spread from one PC to another inside infected local networks. Earlier this year, researchers demonstrated an attack on the Windows Update servers used by large organizations to patch large fleets of computers they operate.
...
[attachment=0]game_over_by_ventious-d73m9mg.gif[/attachment]
Speaking of the forced updates in Windows 10, which by the way, you won't have to put up with it if you follow my instructions here: [url=http://www.techtalk.cc/viewtopic.php?f=30&t=3423]How to disable Windows 10 spyware telemetry logging, [b]including killing off forced Windows updates[/b][/url].
[url=http://arstechnica.com/security/2015/09/nerves-rattled-by-highly-suspicious-windows-update-delivered-worldwide/]Nerves rattled by highly suspicious Windows Update delivered worldwide[/url].
[b]Check out those lovely .MIL and .GOV URLs in this thing! Microsoft said it was an accidental "test". Hahahahhaha riiiight... two ways this could have been:
This wasn't a test, either on purpose or not.
This was a test.
BOTH scenarios are JUST AS BAD!
Bottom line is that Microsoft CANNOT BE TRUSTED TO FORCE AUTOMATIC UPDATES INTO YOUR MACHINES WITHOUT THEM EVEN SAYING WHAT THE MOTHERFUCKING UPDATE IS OR YOU BEING ABLE TO STOP/CHOOSE WHICH UPDATES TO PUT ON YOUR OWN FUCKING MACHINE!
Fuck them![/b]
[attachment=1]suspicious-windows-update.png[/attachment]
[quote]Strange payload raised concerns that Windows Update has been hacked.
...
This [url=https://www.google.com/search?q=gYxseNjwafVPfgsoHnzLblmmAxZUiOnGcchqEAEwjyxwjUIfpXfJQcdLapTmFaqHGCFsdvpLarmPJLOZYMEILGNIPwNOgEazuBVJcyVjBRL&oq=gYxseNjwafVPfgsoHnzLblmmAxZUiOnGcchqEAEwjyxwjUIfpXfJQcdLapTmFaqHGCFsdvpLarmPJLOZYMEILGNIPwNOgEazuBVJcyVjBRL&aqs=chrome..69i57.159j0j9&sourceid=chrome&es_sm=122&ie=UTF-8]Web search[/url], which queries the random-appearing string included in the payload, suggests that it's being delivered to people in multiple regions. The same unexplained and almost certainly unauthorized patch is being reported in a variety of online posts, including this one hosted by Microsoft. [b]The updates appear to be coming directly from servers that are cryptographically certified to be part of Microsoft's Windows Update system.[/b]
[b]"Clearly there's something that's delivered into the [Windows Update] queue that's trusted,"[/b] Kenneth White, a Washington DC-based security researcher, told Ars after contacting some of the Windows users who received the suspicious update. [b]"For someone to compromise the Windows Update server, that's a pretty serious vector. I don't raise the alarm very often but this has just enough characteristics of something pretty serious that I think it's worth looking at."[/b]
White is still trying to obtain a copy of the binary file that gets delivered to people receiving the update. He plans to run it in a restricted environment to see exactly how it gets delivered and what it does once it's installed. One person reported that the update won't download. White said for those who can get the download to work, the payload should be located at c:windowsmsdownloadupdatesoftwaredefu2015�9 estexe_xxxxxxx.exe (where xxxxxxx is the random-appearing characters found in the update bulletin. A Microsoft spokesman said company officials are investigating the reports.
[b]One user has reported installing the update and finding that it rendered the computer largely inoperable.
"My laptop was screwed after the update," the user, ByGodZombie, reported in a comment to this post. "Windows explorer crashes VERY frequently now and most of my programs stopped working even in admin mode. System restore didn't work and I don't have the information I need for a reinstall. Basically whatever it was killed my system and compromised my gear so I wouldn't want to look up anything sensitive to personal data on your machine."[/b]
It's hard to patch a machine when the update mechanism is compromised.
[b]Assuming the worst, that Windows Update has been compromised, it wouldn't be the first time.[/b] The Flame malware reportedly developed by the US and Israel to spy on Iran hijacked Windows update so it could spread from one PC to another inside infected local networks. Earlier this year, researchers demonstrated an attack on the Windows Update servers used by large organizations to patch large fleets of computers they operate.
...[/quote]